What Does The Abbreviation DDoS Mean – distributed denial of service. If you are under DDoS attack, multiple hosts, such as compromised PCs /Laptops /Hosts are leveraged by Cybercriminals to carry out and amplify an attack to stop your services. These compromised PCs/Laptops/Hosts are called bots/zombies.
Cybercriminals can use the processing power and bandwidth of thousands of compromised computers/hosts to form a network of infected hosts where their owners don’t know about the infection and exploitation.
These infected hosts put together are capable of disabling the largest and most sophisticated networks. Cybercriminals use multiple sources to attack a victim. Using this Cybercriminals can amplify the magnitude of the attack and also hide his/her actual source IP address.
Distributed Denial of Service (DDoS) Attacks are a very significant and growing threat to Internet Service availability. Also, it is a growing threat to companies that rely on the Internet Service for business.
Three Types of DDoS Attacks:
Below table shows the denial of service types and metric used to understand attack.
| Attack Type | Metric | Category |
| Volumetric Attack | Bits per second (bps), Gigabits per second (Gbps), flood | Connectionless |
| Protocol Attack | Packets per second (PPS) | Connection-based |
| Application layer attack | Requests per second (RPS), low-rate | Connection-based |
Volumetric—Flood-based attacks that can be at layer 3, 4, or 7. Attacks at L3–4 are usually UDP spoofed traffic.
Protocol Attack – One-sided or stateless UDP traffic
Application Layer Attack – Attacks that exploit software vulnerabilities
Why use DDoS services
DDoS protection service mitigates the risk via protection equipment that is placed in line with the incoming network traffic inside your data center and also configured to work with a burstable cloud-based protection service offered by the OEM.
Nowadays DDoS attack prevention and detection is a basic security requirement, as the number of attacks are increased and the way they affect the business.
DDoS Protection
- Protection against volumetric attack
- Protect against ping flooding
- Protection against vulnerable HTTP traffic
- Protect access to internet-facing applications
High-Level Architecture of DDoS Protection Service
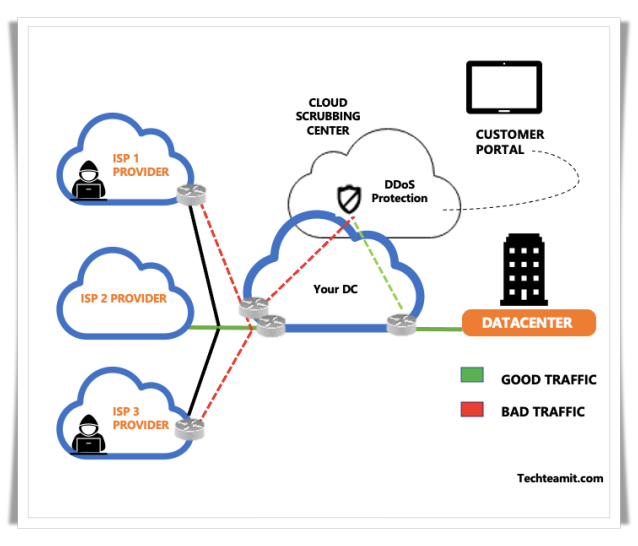
The reference architecture includes multiple tiers of on-premises defenses to protect layers 3 through 7. The network defense tier protects DNS and layers 3 and 4, while the application defense tier can protect high-layer applications.
The cloud component (Cloud scrubbing center) of the DDoS protection solution works as a failsafe mitigation for volumetric attacks that can take more bandwidth on your network.
How DDoS Services can be offered by ISPs/ Data Center Provider:
Example of local ISP/Data center provider offering:
| DESCRIPTION DDOS Protection Service Up to Clean Traffic Per Mbps | UOM |
| Detection, Notification & Mitigation against Unlimited Volumetric Attacks | Per Mbps |
| Reactive Mitigation and Manual diversion of illegitimate traffic once detected | Per Mbps |
| Clean traffic exceeding the subscribed plan limit shall be charged as per add on the rate applicable per MBPS per month | Per Mbps |
| This subscription does not include the Internet Bandwidth and needs to be subscribed separately The minimum Subscription Qty is 10 MBPS | Per Mbps |
At which stage DDoS should be bought & the strategy for it?
Nowadays DDoS security is a MUST for all compliance such as ISO, PCI DSS, other international and local guidelines, etc.
We should have DDoS in place to protect the infrastructure and comply with the need for certification and audit.
We can have a hybrid solution, appliance-based solution, and Cloud-based DDoS Protection solution as a service.
Parameters for OEM/Service Evaluation
Although most of the top OEMs are competent enough, based on our features requirements like hybrid architecture, technology, Security, Scalability, Performance, Manageability, Local and Remote Support, and Industry experience you can find which one is best for your needs and your nature of business.
- Hardware device capability
- Mitigation/cribbing technical features
- Compliance and certification – Cloud scrubbing center
- Network-wide protections
- Server protections
- Signature protections
- SLA on Device
- SLA – Scrubbing center
- Portal and Reporting capabilities
- Training and Documentation
Now based on the above parameter you can evaluate the best suitable OEM/service for your requirement.
Hyperscale DDoS Service
AWS Shield
AWS Shield a cloud-based AWS DDoS service that automatically scrubs bad traffic coming to your network. This protects your applications and APIs from SYN floods, UDP floods, or other reflection attacks.
Azure DDoS Protection
Azure DDoS Protection helps you to protect your Azure resources from DDoS attacks with 24/7 monitoring and automatic network attack mitigation, it can protect single IP or the Network based on your requirements.
Google Cloud Armor
Google Cloud Armor provides built-in protection against L3 and L4 DDoS attacks for your GCP-based services.
Appliance-based DDoS Solutions
- NSFOCUS
- A10
- RADWARE
- ARBOR
Look for the below parameters
- Offering hybrid solution with both On Prime and Cloud
- Scrubbing Center’s global presence
- BGP and DNS options availability
FAQ:
What Does The Abbreviation Ddos Mean?
DDoS stand for – distributed denial of service
What is DDoS?
Cybercriminals use multiple hosts, such as compromised PCs /Laptops /Hosts to carry out and amplify an attack to stop your internet-based services is called DDoS.
Conclusion
DDoS stand for, distributed denial of service. It is recommended to protect your internet-based application against DDoS attacks, use any of the solutions available based on your requirements.
For service providers, it is a must to have a solution to first protect and then offer as a service.
Most of the global enterprise and financial services institutions are adopting hybrid architecture placement for all of their security controls.

