AWS CloudHSM is a cloud service that has a dedicated hardware device serving single-tenant HSM instances. This HSM instance is part of the customer’s Virtual Private Cloud (VPC). You can manage and access your encryption keys.
So, what is AWS CloudHSM? HSM stands for Hardware Security Module, it is a physical tamper-proof hardware appliance. This Hardware Security Module is validated to Federal Information Processing Standards (FIPS) 140-2 Level 3 and based on this hardware device AWS provides AWS CloudHSM as a service.
This lets you manage and access your keys on FIPS-validated hardware in AWS Cloud. The physical security and compliance requirements at the data center are taken care by the AWS.
AWS CloudHSM Architecture
When we are using HSM in private Data Centers providing highly-available clusters is a difficult and time consuming task.
But AWS CloudHSM service makes it easy by providing hardware security modules (HSMs) in clusters mode. In the backend, all the related complications are handled by the AWS team.
When you have a cluster of AWS CloudHSM the other HSMs in that cluster are automatically kept up to date, whenever you perform a task on one HSM.
Once you define an AWS CloudHSM cluster, AWS creates it in the different subnets and availability zones based on your selection.
AWS CloudHSM Quotas:
The below table shows the default quota
| Resource | Default Quota |
|---|---|
| Clusters | 4 |
| HSMs | 6 |
| HSMs per cluster | 28 |
You can adjust the number of clusters and HSM, Per HSM cluster default quota of 28 is fixed.
For more information about cluster quotas
Monitoring And Logs – Amazon CloudHSM sends both logs and metrics to AWS CloudWatch.
Amazon CloudHSM Architectural Best Practices:
- Add redundancy for maintenance purpose
- Deploy your HSMs across many Availability Zones
AWS CloudHSM Pricing:
AWS CloudHSM pricing is very simple to understand. Whenever you deploy an AWS CloudHSM, You will pay an hourly fee for each HSM you provision till the time it is terminated.
Hourly fees range from $1 to $3, depending on the AWS region in which AWS CloudHSM is deployed.
To get real-time AWS CloudHSM cost details, visit the official website.
How does AWS CloudHSM Work?
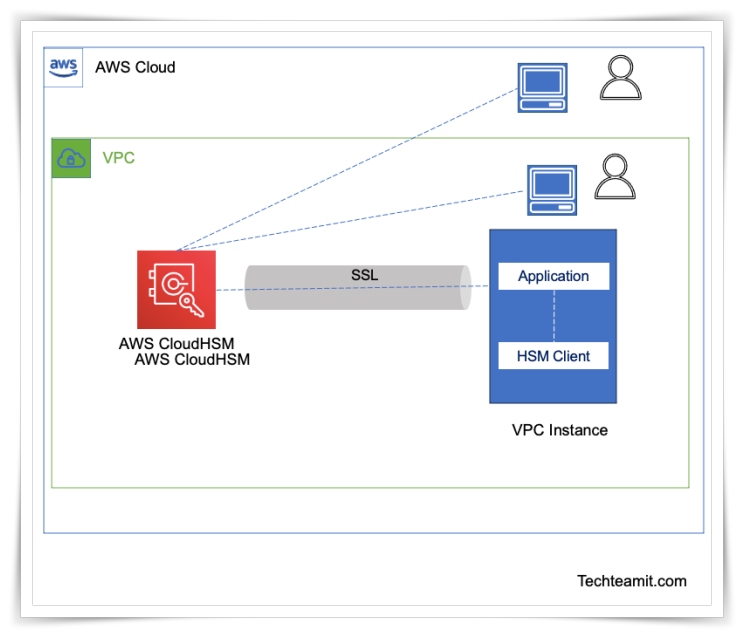
First, you need to create a CloudHSM cluster, once you have your first cluster ready you can start using the AWS CloudHSM service. Your CloudHSM service will have multiple HSMs that are part of multiple Availability Zones over a region.
As discussed earlier, AWS will take care of the automatic synchronization of HSMs in the cluster. Also, it is load-balanced. Each HSM is part of your Amazon VPC and you will have single-tenant access to them. You will be able to use standard VPC security controls to manage HSM access, as they are part of your VPC (Virtual Private Cloud).
By using AWS CLI or AWS CloudHSM API, you can add and remove HSMs from a cluster. Once you have created a CloudHSM cluster, it can be configured on EC2 instances in VPC.
CloudHSM has a tamper detection mechanism to protect encryption keys and thus it is very secure. Therefore, the appliance that is unsuccessful in accessing an HSM partition with admin credentials, erases its partitions to protect.
Video Credit Amazon Web Services
Use Cases Of AWS CloudHSM
Belo list will help you with the CloudHSM use cases:
- Transaction Processing
- Digital Rights Management (DRM)
- Database Encryption
- Public Key Infrastructure (PKI)
- Authentication and Authorization
- Random Number Generation
AWS CloudHSM Features
I still remember when I deployed the first HSM in the data center, the process of procurement to putting in monitored and special lock rack, everything was different and controlled.
In AWS cloud it is simplified and easy. So, let’s go ahead and see some of the salient features offered by this AWS service.
Tamper Proof
HSM is provisioned for single-tenant access and it is a controlled environment within the data center that complies with the U.S. Government’s FIPS 140-2 Level 3 standard. This standard is for the provisioning and operation of cryptographic modules.
Secure Authentication
It provides authentication for key management and important administrative functions. HSM also has multi-factor authentication (MFA).
Scalability
Based on your need you can add or remove capacity on-demand, so managing your HSM needs becomes easy. The HSM capacity management can be done by using the AWS API and AWS Management Console. Kindly refer to the above table for default quota numbers.
No Vendor Locking
CloudHSM makes it easy to migrate keys on or off the AWS Cloud as it is an open solution. When there is a need, you can transfer your keys to other commercial HSM solutions of your choice.
Cloud Based Managed Infrastructure
CloudHSM is AWS cloud-managed infrastructure, The AWS team manages the service that automates administrative tasks, like hardware installation and upgrades, high availability patching, and backups.
AWS CloudHSM Vs KMS
It is important to understand what is the difference between CloudHSM and KMS so that you can select the correct service for your needs. So, let us understand the difference with the help of the below table.
| Comparison Parameter | AWS CloudHSM | AWS KMS |
|---|---|---|
| Complies Standard | Complies with FIPS 140-2 Level 3 | Complies with FIPS 140-2 Level 2 |
| Tenancy | Single Tenant part of VPC | Multi-Tenant |
| Master Key Support | Only HSM Master Key supported | Support for three master keys: AWS Managed, AWS Owned, and Customer Owned |
| Key Accessibility | Only accessible in the VPC | Multi-region accessibility |
| Management | Customer Managed | Managed by AWS |
| Acceleration of Cryptographic Functions | TDE and SSL/TLS Acceleration | Nil |
| Root of Trust | Customer | AWS |
FAQ:
What is the use of CloudHSM in AWS?
It is a cloud-based service offered by AWS for your encryption and cryptographic operations needs.
What does HSM stand for?
HSM stands for Hardware Security Module.
Is AWS CloudHSM free?
No, there are hourly fees, depending on the region in which HSM is deployed.
Conclusion
When you need encryption and cryptographic operations, you can think of consuming AWS CloudHSM. Amazon CloudHSM service provides single-tenant access within your VPC.
It also supports most of the features, like tamper-proof, FIPS compliance, and managed service. And the great news is you don’t need to buy anything upfront, you pay as you use. This was the simplest HSM deployment I have ever experienced.

