We have been using secure shell access to manage our Data Center remotely for a long time, understanding AWS SSM vs SSH will help you make the right choice for you to manage your AWS Cloud environment.
AWS System Manager allows more things to do, making operation and management tasks simple for cloud administrators.
Since SSH bastion hosts used to be an important part of our infrastructure deployment and management, let’s understand what it can do for us.
What is SSH?
SSH (Secure Shell) is a network protocol that is used to manage and access systems remotely. It is used for secure authentication and data transmission using any network. SSH has been used for many years for file transfer, remote system management, and access to remote applications. SSH Bastion host, the system we used for remote access.
SSH (Secure Shell)
So, from a compliance point of view, SSH Bastion helped us remotely access our infrastructure and fulfill needs for different compliance like ISO 27001, PCI DSS, or SOC2.
We can do the below things using SSH Bastion.
1. User Authentication, Management, And Permissions Control
- We can control who can access the SSH Bastion
- We can control time range for user to access the bastion
- We can control source and the destination of the connection
Now to do this the system is connected to organization SSO and ACL is defined centrally.
2. Quickly Revoke Access When Needed
Removing immediate access is one of the key use cases for SSH Bastion
Some of the scenarios are
- Employee changing role within the organisation
- Employees living the organisation
- Compromised account access block
3. Compliance Requirement – Audit Logs
Every auditor will ask for some or other log and SSH Bastion will help you with the required information.
Connection Logs:
Loge information on below
- Users using SSH Bastion
- Users login and logout time
- Source and destination of the connection
- User session information input and output
4. Ease of OS Hardening And Patch Management
- Keeping OS updates to the latest versions
- minimize the outage time during OS updates
- Miner patch upgrade
- OS hardening
5. Securing SSH Bastion Access
As we are working remotely the SSH Bastion host needs to be accessible from anywhere and at any time. The recommended practice is to keep the SSH Bastion host behind the VPN.
Though this adds another layer of management and software which is cost to the company, it reduces the risk of the overall system.
6. Building HA For SSH Bastion Host
As SSH Bastion host needs to be accessible from anywhere and at any time, it demands high availability. Also, during OS upgrade and patch management single system will not work. So it is recommended to have an HA configuration for your SSH Bastion host in different AWS region.
What is AWS SSM?
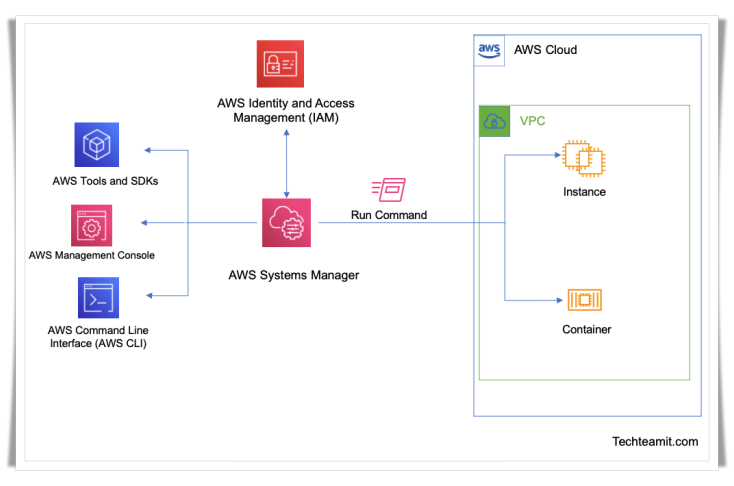
AWS Systems Manager is a complete management solution from AWS, that can be used to manage hybrid and multicloud environments. This solution can be scaled and very secure to use.
With the help of AWS SSM, you can manage EC2 instances and On-Premise systems.
AWS SSM will also give you operational insight into your infrastructure under SSM management. Using this you can detect problems and patching automation. SSM works for Linux and Windows systems. You can use AWS session manager ssh, to connect to EC2.
SSM is a free service from AWS.
To access SSM you can go to the AWS Management Console
Search for the system manager
You will get the below AWS SSM Console
AWS SSM Architecture
AWS System Manager Features
Below are the Key Features of SSM
- You can have a dashboard for your inventory under management.
- You can do inventory management, it can discover the system.
- You can also do an audit on your inventory for software installed.
- You can also do compliance using SSM
Using SSM you can automate certain tasks onto your instances
- Automate shutdown of EC2 instances
- Automate AIMs creation
- Automate Patch Management
- Define maintenance windows
- Run commands on multiple EC2 instances
How SSM Work?
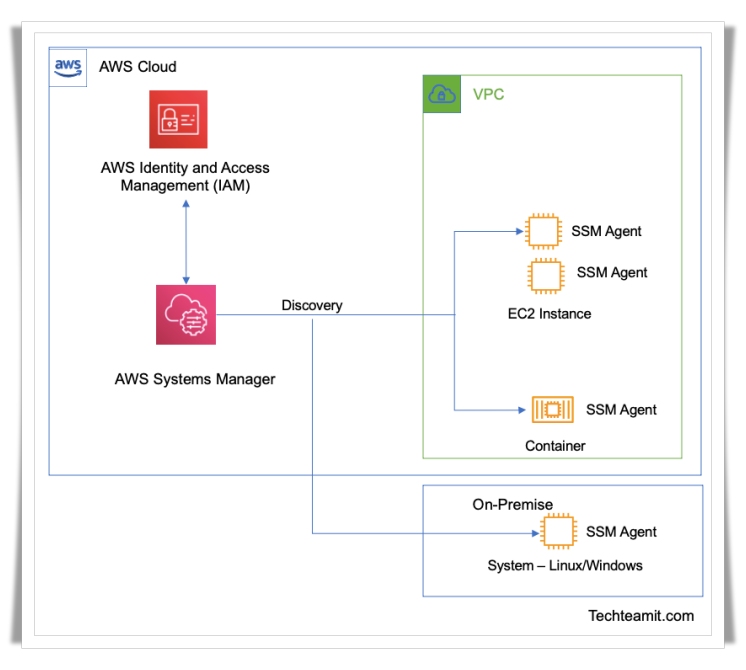
SSM is an AWS service, and we need an agent on the system to work with SSM service. This agent is installed by default when we install Amazon Linux AMI & some of the Ubuntu AMI. You can also manually install the SSM agent on any other Linux or Windows system.
Once the agent is up and running it goes and reports to SSM service and starts working. Remember it needs an appropriate IAM role to start communication with SSM service.
Video Credit Amazon Web Services
SSM vs SSH Comparision
| Parameter | SSM | SSH |
|---|---|---|
| Public IP Required | No | Yes |
| Server Access | Private subnet | Public subnet |
| Authentication Method Used | IAM | .pem Certificate |
| Operational Overhade | Minimum | Moderate |
| Ease of Use | No | Yes |
| Setup Effort Required | Minimum | Moderate |
Conclusion: AWS SSM vs SSH
Now that you understand AWS SSM vs SSH, what is the difference, I am sure you will make the right choice for your connectivity needs.
Both methods are easy and quick. You can connect/access EC2 and On-premise instances. I would choose AWS SSM for one simple reason better security. As a bonus, you can view everything inside the AWS console and its free service.

