If you don’t know AWS STS service or what is AWS STS, don’t worry in this guide I will cover everything you need to know about AWS STS service in detail. I will also cover the purpose it is used for and its benefits for your applications.
Today billions of people use web technology, which is becoming more secure and reliable every day as new technology develops. AWS STS service is one of the technologies that helps secure our access to these applications on the net.
What is AWS STS?
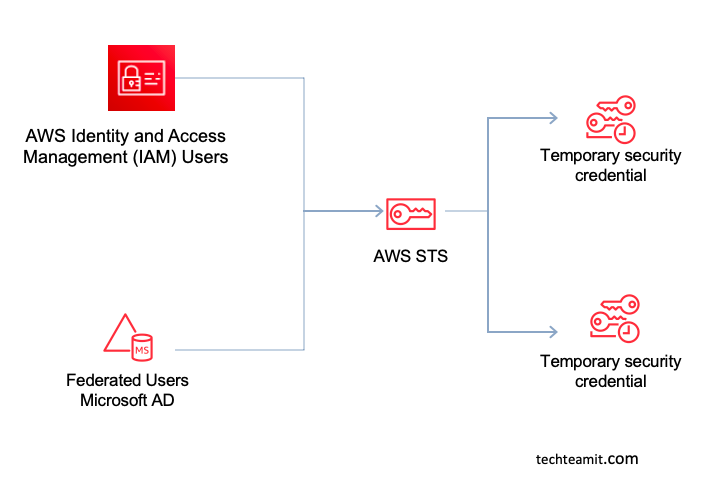
STS stands for Security Token Service, this service on AWS cloud grants temporary access to your organization’s AWS account identity, in simple words secure temporary access to your AWS account and resources.
There are many reasons/use cases you would like to create these limited privilege credentials and use them for granting temporary access. Reasons include cross-platform application working, third-party/vendor access for maintenance and management, and security checks.
AWS STS is available as a global service and the global endpoint is https://sts.amazonaws.com.
Global requests are sent to the US East (N. Virginia) Region.
Why You Need STS
Giving away permanent credentials is always a security concern for most of the organizations. Also, to run business applications in production needs, development, support, and enhancement, and to do this you will need a lot of people who will have access to your application and application code.
Now it is not only your organisation’s people who will need access to your applications but vendors, and OEMs will also need access to support and maintain your application life cycle. Now giving everyone permanent access to your application is not a good idea.
An STS (Security Token Service), can solve this problem by giving temporary access which usually expires in 12 hours by use of AWS STS token. There is a way to extend this access beyond 12 hours and you can configure AWS token service for the same.
Sometimes there are teams that are working together and they are dependent on each other while working on cross-platform applications, they use Security Token Service STS to provision and manage access.
How Do AWS STS Keys Work?
You can access AWS STS programmatically via API calls, with the help of AWS SDK or AWS CLI. The AWS IAM will do API calls global endpoint or regional endpoint (if configured). Once the API call is successful then the SYS key will be generated dynamically.
Response flow of STS request
Access KeyID and Secret keyID – Both the keys are programmatically used to access the AWS Services.
Session Token : STS Service obtain a session with AWS Services with the help of AWS STS keys generated by API call.
Expiration: session expiration with time duration
A unique session token will be generated dynamically by AWS STS for every new AWS service access.
Use Cases For AWS STS Service
There are many use cases, I have taken some of the most important and you will find that AWS STS is worth implementing and provides value for your business applications.
1. Providing and Managing Third-Party Services Access
Developing and managing applications is a very complex process. You will need the collaboration of multiple teams and people to make it work as required by business.
Though you have an in-house application development team you will see many times you will have to give access to external people.
STS can provision this access on a temporary basis and you don’t need to give permanent credentials for your business application to outside users.
When you find the work is done by the external party, you can disable the security tokens and the given access is revoked, now your business application have its privacy in control.
2. Transfer of Power When Required
A lot of time web applications are developed in collaboration with in-house and outsourced teams. Once the application is fully developed and put into introduction the organization will like to have complete control and ownership of the application and data.
Now in this stage organisation would like to take over from the outsourced team that has developed this application.
Now in STS token service you can request the final transfer of power and you will get the complete ownership, now you can reset the credentials as per the need of your organization’s security standards. Now you have complete Control over your business application privacy.
3. Audits & Governance
Your business applications will go through many national and international audits depending upon the nature of your business and your application and data privacy needs.
Now to conduct this audits you will have to give access to your applications, now to do this AWS STS is the best way to give away temporary access to your business application for audit purpose.
This enables auditor to go through your business application and practices without compromising privacy and security. Once the audit is completed you can revoke the access by disabling the security tokens.
4. Stop Unauthorised Access To Your Applications
In a situation where you have a doubt that there is an authorise access happening on your application you can use AWS STS to stop previous access.
All your previous axis will be invalid. Once you have confirm that there is no unauthorised access anymore you can restore your previous access after 12 hours.
Within such a time you have a window to manage your privacy and access if you find there was an unauthorised access to your business applications.
5. Internal Spying
Sometimes there are situations when we have doubt that one of our own employees is leaking the information or capable of doing so and we want to protect our application and information from it.
AWS STS can help us prevent such a situation, you can lock every access given and provide access via STS amazon immediately to only required people.
With the help of these methods, it is easy to track and know who has access, who logged in when, and from where by checking AWS STS access. You can also find out if the breach happened where it began.
6. Mimic An Attack
This is another situation where amazon AWS STS again proves its usability, you want to create a controlled situation where you can test your application security and the capability of your security team and security tools.
If your security team and tools are good enough, they will be able to find this and counter this mimic attack.
If your team and security tools are not able to detect this then you have a bigger problem to address.
Benefits of AWS STS (Pros)
In the use case scenario, we have also seen the associated benefits of AWS STS. Let’s see how some of the core benefits can help you and your business application and help you make the decision to consume this amazing service on AWS Cloud.
Temporary Credentials – Provisioning and Management
The reason why STS service is, that it helps you with generating, distributing, and managing temporary credentials. This is the core purpose of the AWS STS service along with other benefits it offers.
You need to share your AWS credentials on some occasions and you are not confident about sharing your actual AWS credentials with others.
In this scenario, AWS STS helps you with temporary token base credentials that you can share with others for your work. You have control of these credentials when you want to suspend.
Controlled Permissions and Access
The next benefit I want to share is that AWS STS helps you with customizing the access you are providing through AWS STS service.
By using the AWS STS service you can configure when you want people to access your applications, how much access you want to provide, and whom you want to have access to your application.
All this is possible to configure using AWS STS service and can be of great help when there is a need to share the application access.
Additional Control Over Protection
When you are using AWS STS service you are always in control over the access given. Also, when there is a need to stop any or all the access given using the service you can do it immediately.
This additional control gives you the power to protect your application when needed.
Cons of STS
- Single-point control over your applications, and keeping master access is a task.
- Developers of your application are always looking for an updated access code, this can slowdown the development process.
Why You Should Consider Using The Security Token Service
We have seen the benefits it offers to manage your applications in a live environment and the advantages it offers to control the access to your applications. I believe the below reasons will help you to consider using this service for your AWS Cloud.
- Consolidate the Access provisioning and lifecycle management
- Control application usage timeline
- Reduce credentials sharing and theft
Why AWS STS Is More Secure?
- Limited lifetime of temporary credentials.
- Native integration with other AWS Services.
- Support for federation allows you to grant AWS resources access to users that are not part of your AWS account.
- You can limit access to resources that the user or application needs.
- Provides detailed audit logs.
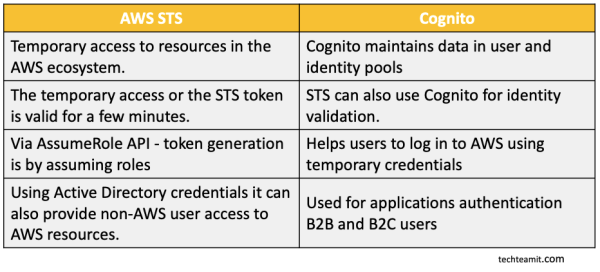
AWS STS Vs Cognito
AWS STS and Cognito services are used to authenticate users using third party applications. In the below table let’s find out how they are compared to each other.
AWS STS Pricing
There is no additional charge for AWS customers to use this service, There are certain regions where the service is default enabled.
However, you can optionally enable the STS endpoint in the region to reduce latency.
FAQ: AWS Security Token Service AWS STS
What benefits does STS service provide your application?
Provision temporary credentials
It helps you to customization capability for permission
Enhanced layer of protection
Why is AWS STS so popular and worth it?
Below thigh makes Amazon STS Service so popular and worth it
Control
Security
Ease of Operation
What is AWSa STS Cost?
AWS STS has no additional cost to AWS customer to use the service.
Final Words
Protecting applications is a need of the day and it affects our business and life in a profound way. Any downtime on applications has a direct impact on business and life too, imagine your flight booking portal is not available, our life has a direct impact from this downtime.
So, knowing about this service will help you to utilize it during your planning and deployment of applications on AWS Cloud.
My intent in writing this information is to share this technical information in simple language so that anyone can understand STS in AWS.
Let me know if this is useful in the comments below.

